Introduction
Imagine a computer that leverages the strange laws of quantum physics to perform calculations far beyond the reach of today's machines. Quantum computing has long been heralded as the next frontier in processing power—poised to revolutionize industries from cryptography and drug discovery to climate modeling. In this post, we explore the evolution of quantum computing from its theoretical roots to its cutting-edge breakthroughs, including the unveiling of the world's first operating system for quantum computers. In doing so, we also cast a critical eye on the security concerns that arise as this technology moves from the lab to real-world applications.
As the quantum era advances, we must address the growing "harvest now, decrypt later" threat, where adversaries collect encrypted data today with plans to break it when quantum computers mature. This post provides a comprehensive overview of how quantum computing has evolved, where it stands today, and what challenges and opportunities lie ahead.
What Is Quantum Computing?
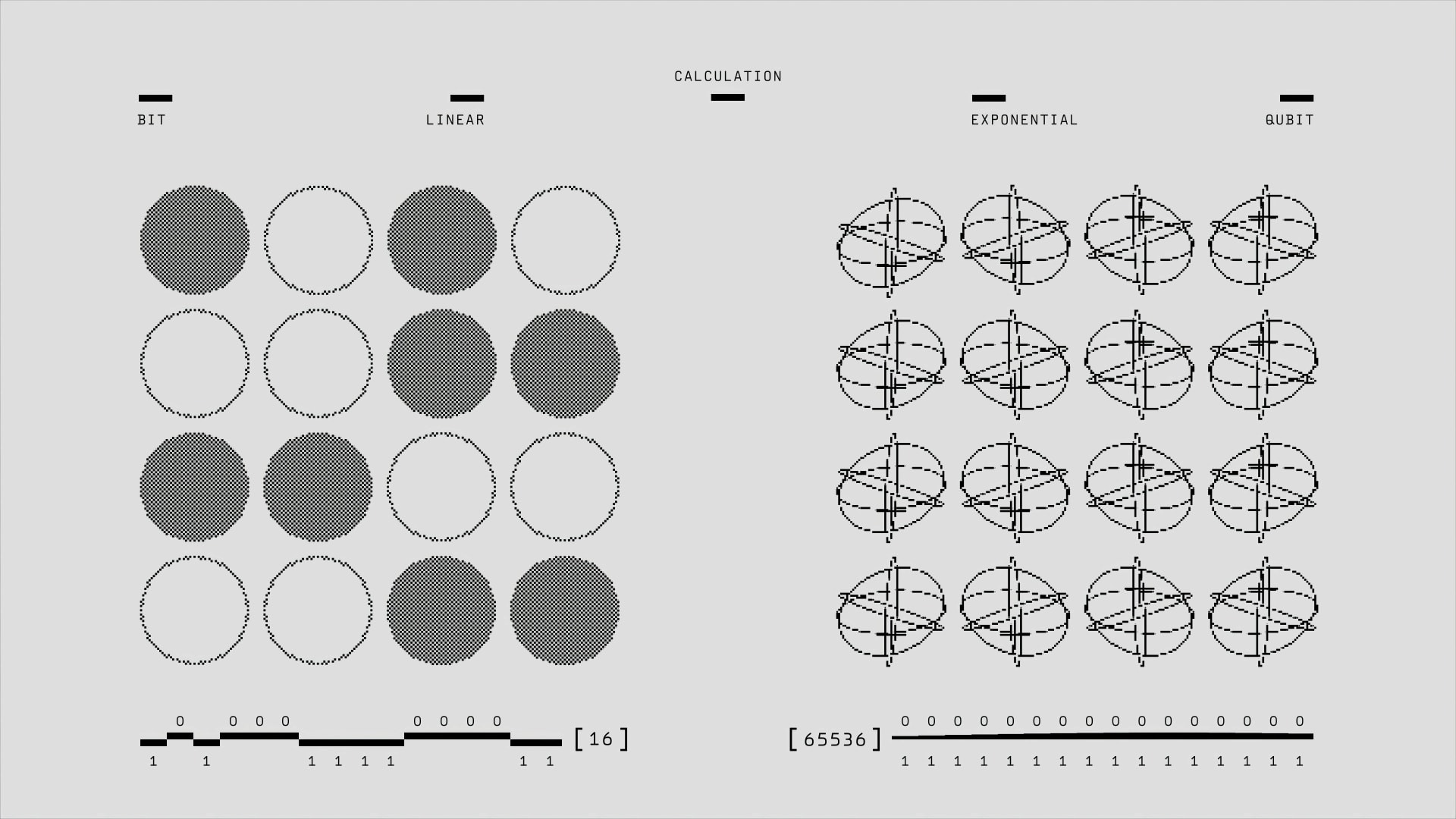
At its core, quantum computing relies on quantum bits or qubits, which differ fundamentally from traditional bits. While a classical bit represents a value of either 0 or 1, a qubit can exist in a superposition—a blend of both 0 and 1 simultaneously. In addition, quantum phenomena such as entanglement allow qubits to be correlated in ways that can exponentially increase computing power.
Key principles include:
-
Superposition
Qubits can hold multiple states at once, allowing quantum computers to process a vast number of possibilities concurrently.
-
Entanglement
When qubits become entangled, the state of one qubit can depend on the state of another, even at great distances, enabling powerful parallelism.
-
Quantum Interference
By controlling the phases of quantum states, unwanted answers cancel out, leaving the correct solution amplified.
This quantum toolkit opens up entirely new methods for computation that could tackle problems far more complex than those manageable by today's classical systems.
Historical Background and Evolution
The idea of quantum computing emerged from the theoretical work of pioneers such as Richard Feynman and David Deutsch in the 1980s. Early research focused on using quantum mechanical principles to simulate physical systems—an idea that would eventually grow into full-scale quantum algorithms.
Theoretical Foundations
Early algorithms, like Shor's algorithm for factoring large numbers, demonstrated that quantum machines might one day break classical cryptographic schemes.
Experimental Progress
As research evolved, laboratories began constructing rudimentary quantum processors using trapped ions, superconducting circuits, and photonic systems. These experiments paved the way for the leap toward practical devices.
Increased Investments
The last decade has seen a surge in public and private funding, driving rapid advancements in building more stable and scalable quantum systems.
"The principles of quantum physics, which govern the behavior of particles at the atomic and subatomic level, are being harnessed to create fundamentally new ways of computing that promise to solve problems beyond the reach of today's most powerful supercomputers."
Developments Over the Last Decade
In recent years, the field of quantum computing has experienced transformative progress:
-
Scaling Qubits
Companies like IBM, Google, and Intel have made strides in increasing the number of qubits in their processors while working to reduce error rates.
-
Advances in Error Correction
Quantum error correction codes are improving, which is critical for achieving reliable, long-term quantum computation despite issues like decoherence.
-
Hybrid Quantum-Classical Systems
New approaches that combine quantum computing with conventional computers are emerging, helping to solve specific problems more efficiently.
These innovations have gradually shifted quantum computing from a purely academic pursuit to an exciting, albeit still experimental, technological frontier.
In 2019, Google claimed to achieve "quantum supremacy" when its 53-qubit Sycamore processor performed a specific calculation in minutes that would take today's most powerful supercomputers thousands of years. While the practical applications of this achievement were limited, it marked a significant milestone in demonstrating quantum computing's potential advantage over classical systems.
Recent Progress and Major Breakthroughs
One of the most compelling developments is the unveiling of the world's first operating system designed specifically for quantum computers. According to a recent article by Live Science, this quantum operating system is intended to manage and orchestrate the complex processes of a quantum machine—and may even pave the way for a future quantum internet.
This breakthrough signals:
-
Enhanced Control
An operating system dedicated to quantum hardware promises better management of tasks like error correction, resource allocation, and system security.
-
Gateway to the Quantum Internet
By enabling seamless machine-to-machine interactions, such software could be foundational to a secure and scalable quantum network that supports new forms of communication.
-
Standardization and Integration
As quantum processors become more common in research and industry, a standardized operating system will aid in integrating quantum technologies with existing digital ecosystems.
This achievement is not just a technical milestone—it also marks a turning point in making quantum computing more accessible and manageable for real-world applications.
Security Concerns in Quantum Computing
While quantum computing holds immense promise, it also poses significant security challenges that require careful consideration:
Threats to Classical Cryptography
Quantum algorithms, such as Shor's algorithm, can theoretically break widely used encryption protocols (e.g., RSA and ECC). As quantum computers become more powerful, the risk of exposure for data encrypted using current standards increases dramatically.
Harvest Now, Decrypt Later
A particularly alarming security threat is emerging in the form of "harvest now, decrypt later" attacks. In this approach, adversaries—including nation-states and sophisticated threat actors—are collecting and storing vast amounts of encrypted data today, with the expectation that once quantum computers become powerful enough, they will be able to decrypt this information.
This presents a serious security risk for sensitive information with long-term value, including:
- Government and defense communications
- Financial transactions and records
- Healthcare data
- Intellectual property and trade secrets
Organizations must consider not only the current security of their data but also its vulnerability to future quantum-enabled decryption.
The transition to post-quantum cryptography is already underway, with organizations developing and implementing cryptographic techniques that are resistant to quantum attacks. This transition should occur well before fully operational quantum computers pose an immediate threat.
Security of Quantum Systems
The physical integrity of qubits is easily compromised by environmental noise, temperature fluctuations, and electromagnetic interference. Securing the hardware environment is paramount for reliable operation.
Additionally, as seen with the new quantum operating system, designing software to manage quantum processes securely is a new challenge. The operating system must not only optimize performance but also integrate robust security protocols to prevent malicious interference and ensure the integrity of quantum computations.
Quantum Communication and the Quantum Internet
On the flip side, quantum principles are being harnessed to create virtually unbreakable encryption methods through Quantum Key Distribution (QKD). However, integrating quantum-secure communications with traditional networks remains a complex challenge.
As the promise of a quantum internet draws near, ensuring that this new network infrastructure is safe from novel attack vectors is critical. New security frameworks and protocols will be required to protect both data exchange and control signals across quantum networks.
Balancing Innovation with Risk
Ultimately, the evolution of quantum computing demands a balanced approach: embracing the technological revolution while proactively addressing its inherent security risks. This involves not only developing post-quantum cryptographic solutions but also ensuring that new quantum platforms incorporate comprehensive, multi-layered security measures from the outset.
Future Outlook and Challenges
Looking ahead, the horizon for quantum computing is both exciting and uncertain:
-
Expanding Applications
From revolutionizing drug discovery and financial modeling to optimizing complex supply chains, quantum computing promises to tackle problems that are currently unsolvable by classical computers.
-
Scalability and Error Correction
Despite remarkable progress, challenges remain in scaling up qubit counts and ensuring long-term error correction. Overcoming these obstacles is essential for the practical deployment of quantum systems.
-
Security as a Dual-Edged Sword
The same technology that threatens current encryption methods also offers new avenues for secure communication through quantum-resistant protocols. However, the transition must be managed carefully to avoid an interim period of vulnerability.
-
Infrastructure Integration
The eventual integration of quantum systems with existing digital infrastructure—and possibly a quantum internet—will require a whole new ecosystem of software, hardware, and security practices.
-
Economic and Ethical Considerations
As with any disruptive technology, quantum computing raises questions about the economic implications of its adoption and the ethical considerations surrounding data privacy and access to advanced computational power.
Conclusion
Quantum computing is transforming the boundaries of technology, promising an era of unprecedented processing capabilities alongside equally profound security challenges. The journey from theoretical concept to operational systems—including innovations like a dedicated quantum operating system—highlights both the immense potential and the critical hurdles that lie ahead.
As we continue to unlock the secrets of the quantum realm, a delicate balance must be struck. The drive for machine-optimized performance must be tempered with robust security measures designed to protect both the data and infrastructure of tomorrow. In this evolving landscape, technology leaders and security experts alike must collaborate to ensure that quantum computing not only propels us into a new era of discovery but does so in a way that safeguards the digital world we depend on.
"The balance between quantum innovation and digital security will define how successfully we navigate this new frontier. Organizations must prepare today for the post-quantum world of tomorrow."
What are your thoughts on the balance between quantum innovation and digital security? Join the conversation and share your insights as we navigate this quantum frontier together.